Browsers are implementing ever more sophisticated security measures to prevent websites from creating profiles to serve with targeted advertisements. Despite their effectiveness, it is difficult to fully ensure that a user cannot be tracked by hijacking a basic web browser function. Evidence that has been shown with this new demonstration of security researchers Favorite icon It can be diverted for this purpose.
Four researchers from the University of Chicago were able to create only one unique profile Favorite icon, These icons are associated with a site that is displayed in the web browser’s interface. In all browsers, they can be displayed on each tab, to better identify the site in the tab bar and they are also found in Favorites.
In Favorite icon Are provided by websites. The URL of the image is indicated on each page and the browser downloads it to be displayed in the correct location. To avoid downloading this resource each time, all browsers add it to the cache, a local folder where all pictures are stored for future use. When you return to the site, this local file is loaded, not a remote copy.
Cache of Favorite icon The browser is managed differently from the cache, which contains other website resources, such as pictures or JavaScript files. The latter can be emptied at any time by the user and the browser regularly takes care of the cleanup. This is not the case for site icons, which are not deleted at the same time as the browser cache. In addition, the same cache is used for normal and private sessions, there is no separate storage.
The last required bricks follow browser redirects. On most web pages, Favicon Is directly populated as a reachable image, but it may also be that the URL is redirected. In this case, the server returns the browser to another URL, which may be a picture or some other redirect. There is no limit on the number of redirects taken to get an image, which allows you to create a profile by multiplying them.
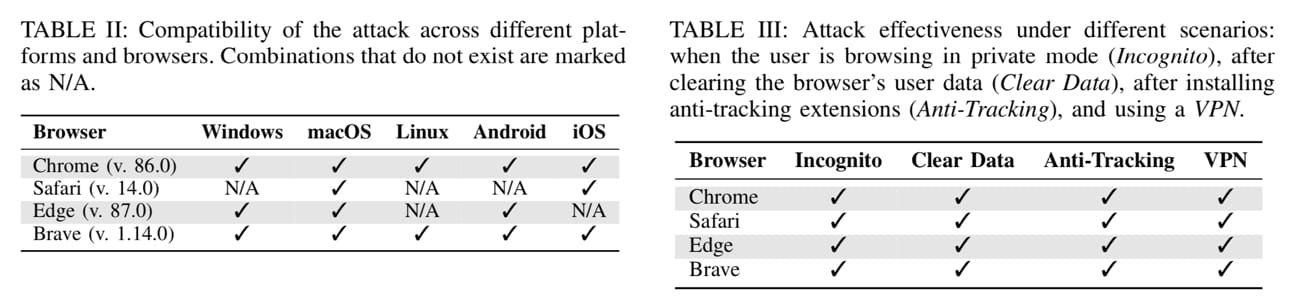
Security researchers have thus created a device that relies on multiple redirects to store in cache. Favorite icon. The sequence of images establishes the profile: each user has separate files, which make it possible to identify them and, for example, then display advertisements that fit their known interests. According to him, Chrome and its variants (including Microsoft’s Edge and Brave) are affected, as well as Safari on MacOS on iOS, but not Firefox due to a bug that prevents the browser from properly using its cache.
However, I noted during my tests that Favorite icon When I cleaned the browser cache it was completely cleaned by Safari. Apple has updated its browser twice from the version used by security researchers, perhaps in the meantime closing the blame. This article also provides several solutions to the creators of browsers to prevent this attack on their security. Using a separate cache for private browsing and more complex ones like links are as simple as Favorite icon Cookies to remove both at the same time.
Either way, browsers are currently susceptible to this type of attack and will need to be updated to block it. No need to panic, however, the evidence given by these security researchers does not mean that such tracking is easy to create, especially on mobiles where it takes an average of four seconds to create a profile and then access it later. However, this is an interesting example of the hijacking of seemingly intuitive work by browsers.
This is not the first example, moreover. More recently, it was Do Not Track, an option that allowed Internet users to ask sites to follow them now, which had been hijacked. Not only were the sites not obligated to honor this choice, but it was also used to feed profiles for advertising purposes, thereby predicting their disappearance.

Prone to fits of apathy. Music specialist. Extreme food enthusiast. Amateur problem solver.




