What digital risks do companies see in terms of security?
Currently, most of the remote workers work from home. An important piece of information is that members of remote teams often do not know about cybersecurity. In this sense, they are unlikely to have intrusion detection systems and firewalls on their personal networks.
In a study of SafeGuardCyber Through a survey, digital risk was analyzed. It was held in October 2020 among 600 senior IT professionals to follow the new digital reality of the workplace due to the COVID-19 epidemic. One of them is, without doubt, more introduction of telecommunications from home. The survey shows that despite perceived digital exposure around unauthorized applications, only 18% of respondents named security a concern.
57% cited Microsoft teams and Slack platforms as one of the threats that pose the greatest risk. Closely followed is other marketing technology with 41%.
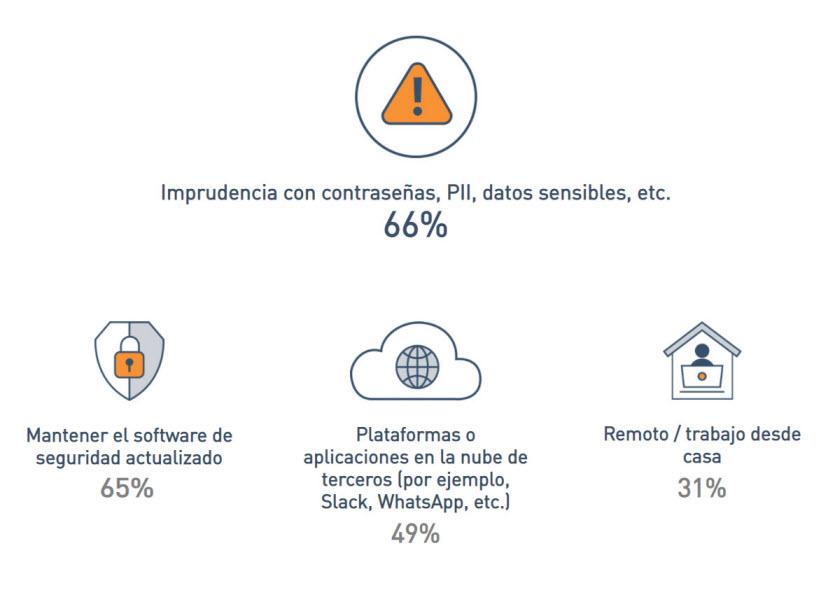
Personal social networks of officers with 26% were also factors considered by the respondents. Concerns about protecting digital infrastructure, carelessness with passwords with 66%, and keeping software up to date with 65% occupy the top positions. It follows concerns about cloud application platforms such as 49% with Slack, and remote work from home with 31%.
But that’s not all, those senior IT professionals were also concerned about:
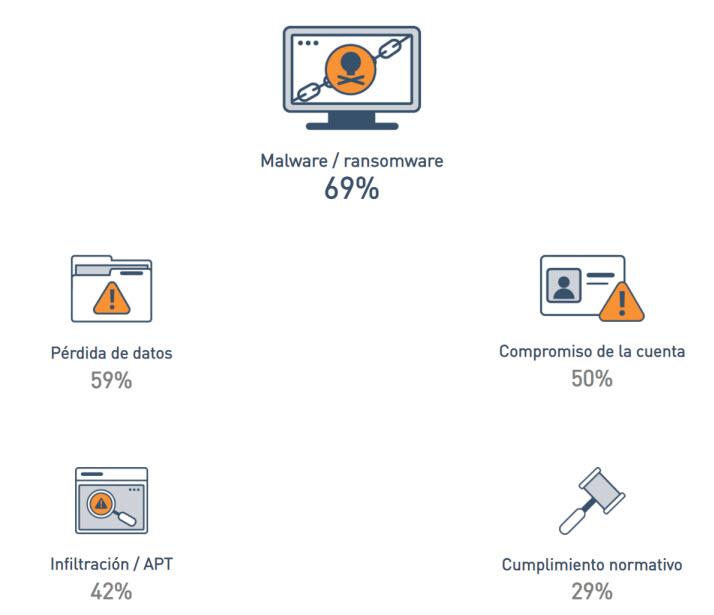
- Malware and ransomware accounted for 69% of attacks.
- 59% for data loss.
- Account commitment 50%
- Infiltration / APT 42%.
- Regulatory compliance 29%.
However, this does not mean that we are under strict stress. By understanding the risks of data hacking and the steps we can take to protect ourselves, remote teams can reduce the chances of your business becoming just another hit state.
Rise of data theft
The 2019 Riskbed Security Cyber Risk Analysis data breech report found 3,813 violations that exposed more than 4.1 billion records. The number of reported violations in those numbers increased by 54% and the number of records increased by 52% over the previous year.
Cyber Criminals do not look for specific content when stealing databases. Your goal is to obtain corporate business plans, credit card details and personal information that may be valuable to you. A Cisco report found that many important companies are not protected. The report revealed that 62% of the respondents’ companies either did not have a cyber security strategy or their strategy was passive or outdated.
Keep in mind that data hacking can come from inside or outside the company, and our cyber security strategies must include many components. We cannot base all security on intrusion detection systems, however good they may be. In that sense it is not fair because we will protect ourselves with a single card.
Internal data theft risk in companies
Verizon’s 2019 Data Breach Investigation Report found that 34% of data breeches were caused by company insiders. However, it should be noted that inside data hacking is not always intentional. According to Kaspersky, 52% of companies believe that their workers are their biggest security weakness. Thus negligent action and therefore human error endangers the security strategy.
Reasons why employees may be careless:
- Do not change passwords regularly.
- Do not use a VPN on a Wi-Fi network or work from home.
- Your devices are not up to date and not properly protected.
- Theft of mobile or portable devices.
Improvements we can make to avoid internal theft
Remote teams and other personnel working in company offices should have an action plan. Therefore, they should have training and protocols so that they can know how to work. Thus, a very important part CContinuous appeasement in company. This cyber security training can be online or face-to-face, must be continuous over time and must be mandatory for all employees. It is important to include here information about how violations occur and how we can protect ourselves. This is a continuous career in which we must be informed and take courses on phishing, scams and other security matters from time to time.
Also we should Create guidelines and action protocols regarding cyber security. What we need to do is create a document in which they explain:
- How information about security issues is communicated.
- The company’s access security protocol.
- Performance of employees in the face of various security threats.
- Multi-factor authentication and VPN access.
You also have to Promoting a culture of honesty, In which the worker is made aware that the sooner this information is reported to the company, the sooner the data can be protected and the loss of the breach can be minimized.
How to protect your business from external data theft
Next, we are going to offer a series of proposals that can protect us from cyber criminals who try to steal data from outside the company. These measurements can also be used by remote computers. Company should be taken out Safety Management of Used Equipment. In this sense, he should guarantee security measures for his employees’ smartphones, computers and laptops.
Employees should conduct Good practice in creating strong passwords. Therefore, from RedesZone we recommend creating a password with these features:
- Contains a minimum of 12 characters.
- It includes letters, numbers and symbols like $.
- Should include upper and lower case
In addition, these passwords must be changed from time to time, ensuring that no other uses have been used by us before. An important element is We should work with vpn. Thus, our connection will be encrypted and it is like having an encrypted tunnel inside which no one can read it. In public Wi-Fi networks, workers must use it even if they are not working, especially if the equipment is used for work at some point.
Is another good practice Use cloud-based encryption software To transfer our data from the cloud. Nor should we forget Multi factor authentication, We should not delegate security for the use of username and password only. When possible, it should be active in accounts that we use MFA or 2FA authentication. Finally, if remote control devices follow this series of tips, they will greatly improve their security.

Prone to fits of apathy. Music specialist. Extreme food enthusiast. Amateur problem solver.