Pegasus spyware is still talking about it. Spyware 36 journalists developed by the NSO group were used to infect and monitor iPhonesal JazeeraAll of Qatar’s news channels polite with their big neighbors (a journalist)Al Aarabi TV Located in London were also targeted). The governments of the United Arab Emirates and Saudi Arabia sponsor these intrusions, according to Citizen Lab, which disclosed the case.
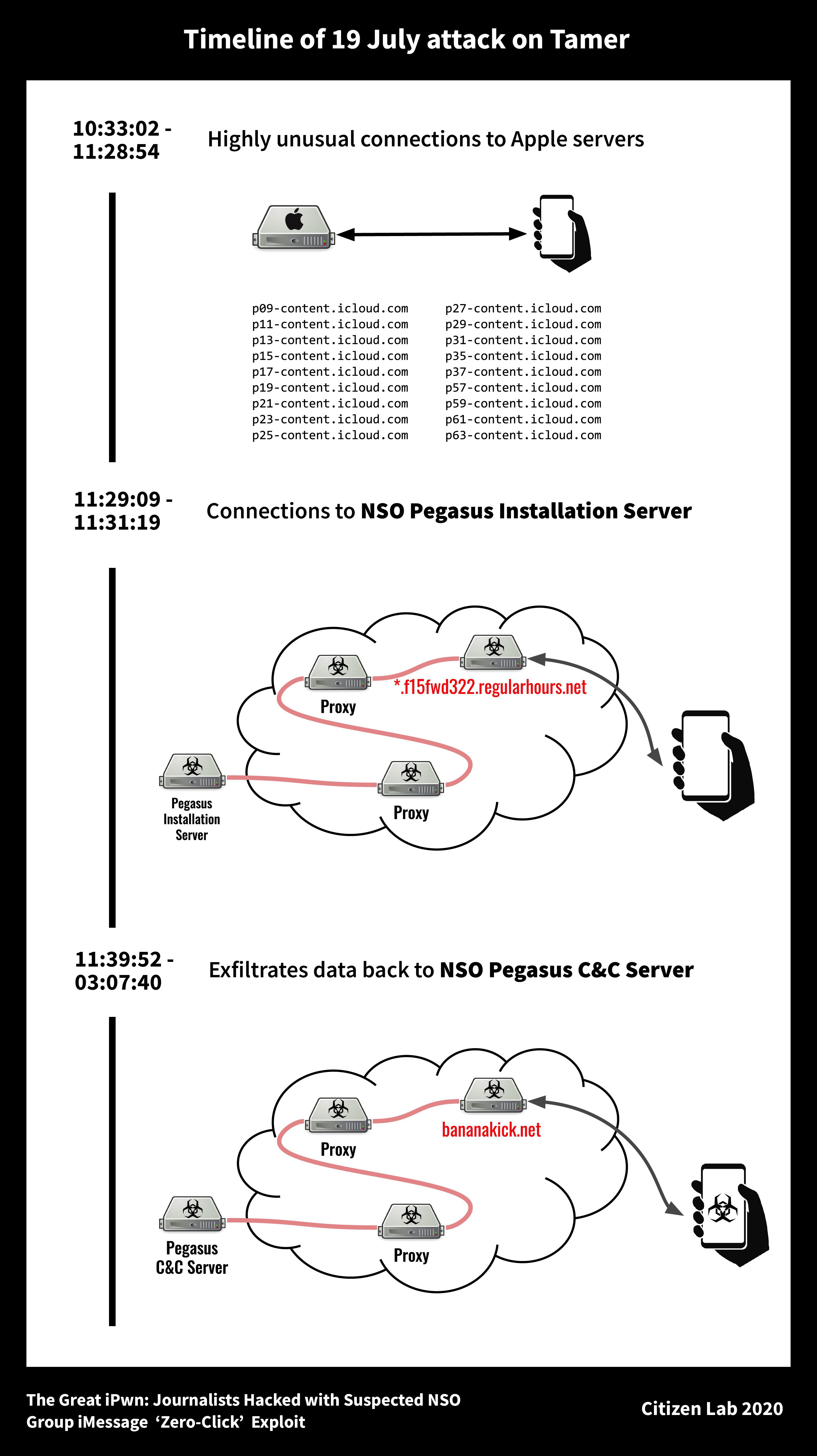
There were attacks in July and August this year. To break into the smartphones of their victims, hackers exploited a flaw named Kismet that contained a “zero day” vulnerability (with no known problems) in the messages. this was it Revised With iOS 14: As always, we can only recommend updating your devices regularly.
The flaw is rather spectacular because it involves no prior action by the target user: all you have to do is receive a text message … one of the reportersal Jazeera It is suspected that his iPhone was being hacked and sought help from Citizen Lab to find out. The researchers set up a VPN to find out the details of the communication received and sent by the device. It is thanks to this method that they were able to discover Pot aux roses.

Unlike other applications built into iOS, the “sandbox” of the messaging application tends to overflow, offering a gateway to thugs to be embedded in the operating system and put money into the mix. The infrastructure used for these attacks is based in the United Kingdom and in many European countries including Germany, Italy and France, through cloud providers such as Digital Ocean. Apple was made aware of this discovery and investigated the case.
The NSO Group wants to continue its faith to ensure that its software is only used to monitor criminals and terrorists. But examples from the past few years show that governments and their security agencies are not stuck with it (read: Jamal Khashogi’s iPhone used to spy on him?).




